Numb3rs 514: Sneakerhead
In this episode, the team is trying to find a collectible pair of sneakers that is stolen from a Brazilian consulate. They are able to narrow down the list of suspects to those that are familiar with ways of beating the biometric security system. When the team finds a warehouse full of counterfeits, they hope that one of the pairs is the authentic Primers. Charlie uses hyperspectral imaging to figure out that actually all of the sneakers are counterfeits. After further investigation the team is able to trace the sneakers back to the original owner.
Biometric Door Locks
Biometric door locks are the next big thing. Soon enough many of us will stop carrying keys to our house, car, office, etc. Biometric door locks can be taught to recognize authorized person's fingerprint, iris pattern or even voice. Biometrics, in general, is a method for recognizing humans based upon certain inherent traits, whether they are physical (fingerprint, face recognition, DNA, etc) or behavioral (voice, type of movement).
Over the past few years there has been great effort made in order to try to perfect the art of using somebody's voice to definitively recognize a person. Voice biometrics has great advantage over other methods since it is easy to implement and authentication can be performed remotely via a telephone or internet. A typical human voice is formed when sound waves, generated by airflow from the lungs, are carried by the wind pipe through the vocal cords out through the vocal tract. As the sound passes through the vocal tract, its frequency is altered by resonance.
The most important factors of speech that make this technology possible, are speaking rate and dialect. However, when using this technology, caution is in order. Some experts do argue that speaker recognition is not an accurate method of identification, as compared to DNA and fingerprint analysis. Furthermore, the human voice can be altered by aging, stress, cold and allergies. Also, as you saw in this episode, the thieves were able to crack the biometric security system, since the voice of the authorized person was freely available online. Thus it is advised to use voice recognition technologies primarily as an easy to use and non-invasive method of verification.
Optimized Searching
When Charlie is faced with a set of suspects, he tries to find the ones that are most likely to have committed the robbery by optimized searching technique.
A searching algorithm is a procedure that takes an input data and a target and tries to efficiently find the target in the data. The brute force algorithm consisting of looking through every peace of data is usually very inefficient. Often, more efficient algorithms exist. These algorithms try to exploit the structure of the data. One of the most prevalent data structure is that of a list. In this case, the brute force algorithm is a linear search, which looks through every element one by one, until the target is found. This algorithm works for any list. However, what if there is extra structure in the data? For instance, what if the data is already sorted in some order? In this case, a less naive algorithm is available, called binary search. It runs much faster than the linear search algorithm, but has the disadvantage that the list must be presorted. The idea of the algorithm is outlined in the following activity.
Activity: Let's consider a sorted list of numbers
S={2, 5, 7, 9, 12, 84, 100, 134, 201, 234, 235} but say we don't know which numbers are in the list. All we know is that there are eleven of them in S, and they go in increasing order. Now say we are looking for the position of the element "12" in this list. What we are allowed to do, is to look at a number in any given position (ex: if we look at position six, we will see that 84 is there). The idea is not to look through the whole list.
- The first step would be to figure out whether "12" is in the first half of the list or the second half. How can you do that by only looking at one of the numbers?
- Here we know from step 1, that our target "12" is in the first half of the list (hence we are left with five possible positions). How can we narrow this down to two possible positions, by only looking at one of the numbers?
- Finally, now that you narrowed it down to two possible positions, you only need to look up one of them to find out where "12" is. Why?
Hyperspectral Imaging
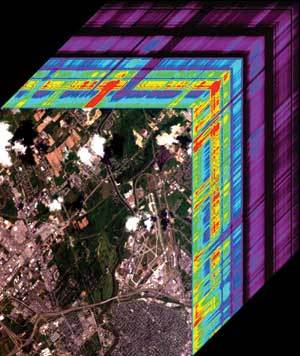
"An airborne image, with its spectrum shown as a colored stack beneath each pixel, creates a three-dimensional image cube that emphasizes the spectral nature of the data." (Source of data: NASA Jet Propulsion Laboratory, California Institute of Technology)
The team found a warehouse used to create counterfeit sneakers from the original Primers. Charlie was asked to figure out which pair out of hundreds was the original one. He first suggested to use cross-sectional analysis, then buoyancy, and then finally he came up with a none-invasive way to compare the sneakers - hyperspectral imaging.
Hyperspectral imaging is used to detect certain types of light in the electromagnetic spectrum. Not only is it able to determine the visible light (that you and I can see), hyperspectral imaging also detects ultraviolet and infrared lights. This helps to determine the material makeup of the object. Since some objects have unique "fingerprints" across the electromagnetic spectrum, hyperspectral imaging can be used to authenticate collectible items. Hyperspectral imaging is currently widely used in historical manuscript research and surveillance. In fact, this technique can be used for military surveillance purposes. One such example, is that using hyperspectral imaging one can identify the target from a plane, without being noticed from the ground.
Charlie tried using this technique, but sadly, it turned out that none of the sneakers in the warehouse were the original Primers.
Reference:
http://www.ece.uah.edu/biometric/voice_recognition.htm
 "An airborne image, with its spectrum shown as a colored stack beneath each pixel, creates a three-dimensional image cube that emphasizes the spectral nature of the data." (Source of data: NASA Jet Propulsion Laboratory, California Institute of Technology)
"An airborne image, with its spectrum shown as a colored stack beneath each pixel, creates a three-dimensional image cube that emphasizes the spectral nature of the data." (Source of data: NASA Jet Propulsion Laboratory, California Institute of Technology)