A some number of spaces
to the right, and start the alphabet from there, wrapping around when
we get to Z. The way in which the shifted alphabet lines
up with the un-shifted alphabet is the cipher. For example, a three
shift looks like:
plaintext: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z ciphertext: X Y Z A B C D E F G H I J K L M N O P Q R S T U V WIn this example, the message:
WHAT KIND OF CAKE SHOULD WE HAVE? ALICE.from Alice to Bob would look like
TEXQ HFKA LC ZXHB PELRIA TB EXSB? XIFZB.Suppose that Bob responds to Alice's message with:
GLB OBXIIV IFHBP ZELZLIXQB ZXHB. YLY.How do we go about decrypting this message? It's easy, we just swap the roles of the alphabets above:
ciphertext: X Y Z A B C D E F G H I J K L M N O P Q R S T U V M plaintext: A B C D E F G H I J K L M N O P Q R S T U V W X Y ZNow we can decrypt the message:
JOE REALLY LIKES CHOCOLATE CAKE. BOB.
At this point, you might ask what happens if we shifted left instead of right. In general, that would give us a different cipher. However, since we wrap around at the end, every left shift is just some right shift, but probably for a different number. We'll talk more about this later.
We have our first cipher, and already, we see that it is a bit tedious
to encrypt and decrypt the message. One way to help ease this process
is to think of each letter as a number, with A
corresponding to 1, B to 2, and so on up to
Z corresponding to 26.
Then, we can represent a shift of ![]() to the right as
simply adding
to the right as
simply adding ![]() to each number. For
example, suppose Carol wants to send the following message to Dave,
with a shift of 7:
to each number. For
example, suppose Carol wants to send the following message to Dave,
with a shift of 7:
PARTY STARTS AT NINE PM. CAROL.First, she writes out the message in number form:
16-1-18-20-25 19-20-1-18-20-19 1-20 14-9-14-5 16-13. 3-1-18-15-12.Now all she does is adds 7 to each of the numbers:
23-8-25-27-32 26-27-8-25-27-26 8-27 21-16-21-12 23-20. 10-8-25-22-19.Does anyone see a problem with the encrypted message above? If you spotted that we don't have a letters corresponding to numbers bigger than 26, good for you. There is an easy fix to this problem, however. Remember originally that we 'wrapped around' once we got to
Z. The number equivalent to wrapping around is
subtracting 26 if the number is too big. Thus, Carol's encrypted
message becomes:
23-8-25-1-5 26-1-8-25-1-26 8-1 21-16-21-12 23-20. 10-8-25-22-19.To decrypt this, Dave simply subtracts 7 from each of these numbers and adds 26 to anything he gets that is negative. As you will try, this is much faster than our first method which used only letters.
Unfortunately, the messages we have looked at so far are particularly vulnerable to attack. In particular, including punctuation marks gives clues to an attacker about the structure of the sentence. Also, without regrouping our letters into uniform blocks, attackers can know the length of words. Since there aren't very many one and two letter words in the English language, this could be a big help. Finally, putting dashes between numbers shows an attacker when one number ends and the next begins. Fortunately, there is an easy way to fix all of these problems at once. We start by renumbering the alphabet with two digit numbers and also assigning numbers to other common symbols and punctuation marks:
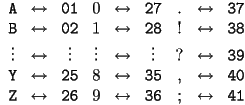
Next, we adopt our convention of grouping our message in blocks four
digits. Note that this may require us to put an X at the
end of our message (why?). Combining this with the renumbering should
fix the problems we mentions. Lets look at an example.
Suppose Alice wants to send Bob the following message with a shift of 4:
I have 150 balloons! Alice.XHere, we added the
X at the end so that the total number
of characters would be divisible by 4.
Converting this into numbers we get:
09 08-01-22-05 28-32-27 02-01-12-12-15-15-14-19-38 01-12-09-03-05-37-24Next we add 4 to each number:
13 12-05-26-09 32-36-31 06-05-16-16-19-19-18-23-4 05-16-13-07-09-41-28In our first attempt using numbers for letters, numbers larger than 26 had no meaning so we had to adjust those. Under our new scheme, however, the numbers from 1 to 41 all correspond to some symbol. It is only the numbers larger than 42 that we need to worry about now. We handle them as before: we subtract off the largest number which means something. In this case, that number is 41. Looking back, we need only replace the 42 which corresponds to the
!
shifted by 4:
13 12-05-26-09 32-36-31 06-05-16-16-19-19-18-23-01 05-16-13-07-09-41-28Now, all that is left to do write our message in uniform blocks, each with 4 digits:
1312 0526 0932 3631 0605 1616 1919 1823 0105 1613 0709 4128